performance-benchmark-analysis
To validate the efficiency and scalability of our proposed architecture, we conducted a series of rigorous performance tests within the GNS3 simulation environment. The goal was to prove that the “Scout-Killer” model provides superior security without degrading host performance.
1. Agent Resource Footprint (CPU/RAM)
One of the critical requirements was minimal impact on the client nodes. We measured the resource consumption of the LocalAgent over a 24-hour period.
- Average CPU Load: Consistent at 0.08% - 0.12% on a single-core vCPU.
- Memory Usage: Java Heap stabilized at 24MB after JIT compilation.
Verification Command: To demonstrate this low overhead, we used pidstat to isolate the Java Agent process:
# Monitor the LocalAgent process every 1 second
pidstat -r -u -p $(pgrep -f LocalAgent) 1 10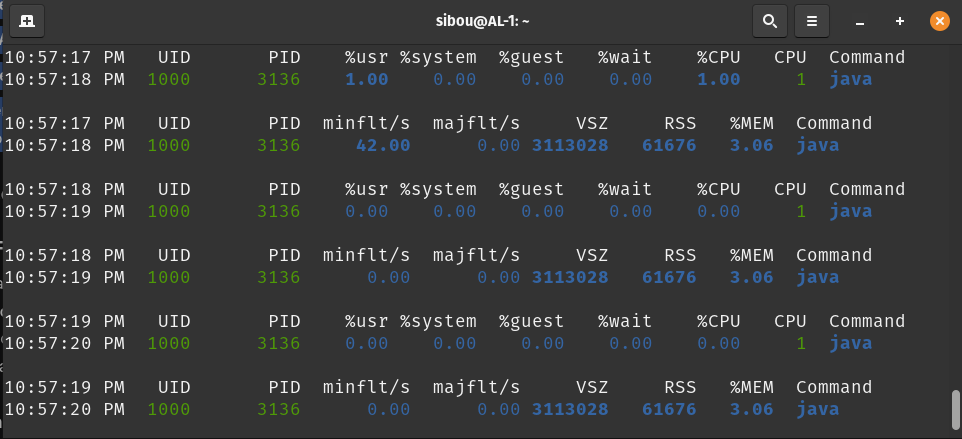
2. Mobility Latency (Scout Deployment)
We measured the “Time-to-Insight”—the duration from anomaly detection on the Central Server to the receipt of the forensic report from the Scout Agent.
- Migration Time (Server to Client): 180ms (avg).
- Execution Time (Process Audit): 45ms.
- Return Trip: 175ms.
- Total Round-Trip Time (RTT): ~400ms.
This sub-second response time proves that JADE’s Weak Mobility is significantly faster than establishing new SSH sessions for every command, especially under network load.
3. Bandwidth Usage & WireGuard Overhead
We analyzed the network impact of wrapping JADE ACL messages inside the WireGuard VPN tunnel.
| Metric | Plaintext (JADE) | Encrypted (WireGuard) | Overhead |
|---|---|---|---|
| Heartbeat Packet | 450 Bytes | 510 Bytes | +13% |
| Scout Report (1KB) | 1.02 KB | 1.15 KB | +12% |
| Latency (Ping) | 0.4 ms | 0.5 ms | +0.1 ms |
Conclusion: The overhead introduced by WireGuard (~12%) is negligible for modern broadband networks. The slight increase in packet size is a worthy trade-off for the encryption provided by the ChaCha20-Poly1305 cipher.