password-reset-otps
Another critical issue discovered in the forgot password functionality is that once an attacker obtains a valid user ID, changing the password requires only an OTP that is directly displayed as a modal on the web page. This means there is no secure delivery or verification of the OTP, and it is exposed openly to anyone requesting it.
Using the previously obtained JSON file containing all user IDs, I was able to easily trigger password resets for any user by simply submitting their ID and retrieving the OTP from the response. This flaw effectively allows an attacker to compromise the entire user base without needing access to the users’ email or phone.
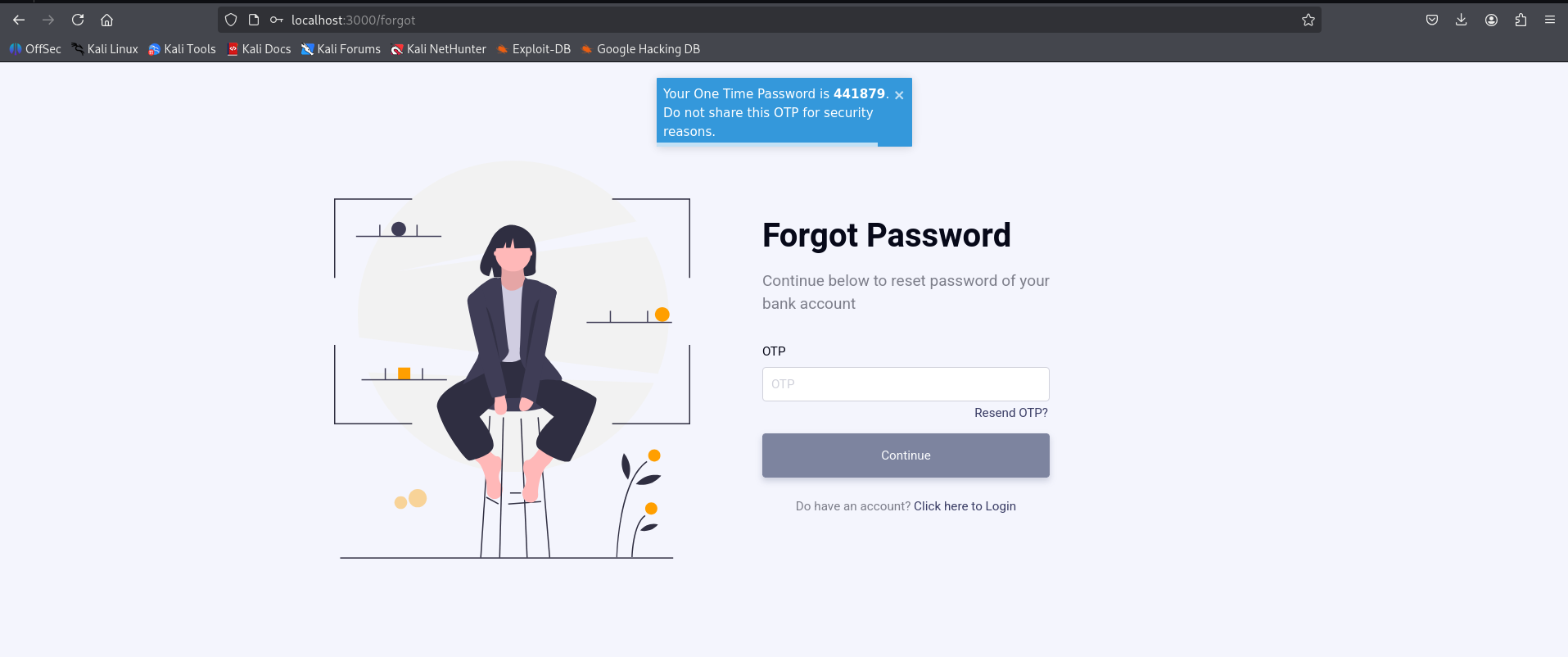
This is a Critical issue (CVSS ~9.0) because OTPs are exposed directly in the response, allowing attackers to bypass secure verification and reset passwords instantly.
As a remedy, we should:
- Never expose OTPs in API responses or on the client side. OTPs should be securely delivered via out-of-band channels (email, SMS) and verified server-side only.
- Implement proper OTP expiration, rate limiting, and logging to prevent abuse.