fake-old-password-verification
While reviewing the password update functionality, I discovered a critical vulnerability: the application does not verify the correctness of the current password before allowing a user to update it.
Although the frontend form includes a “Current Password” input field (as shown below), the backend fails to validate its contents. Submitting any value in this field — including completely incorrect or random text — will still result in a successful password change, as long as the user is authenticated.
This effectively means that once a user logs into their account, they can change their password without knowing their current one, removing an important security barrier against session hijacking, token theft, and similar post-authentication attacks.
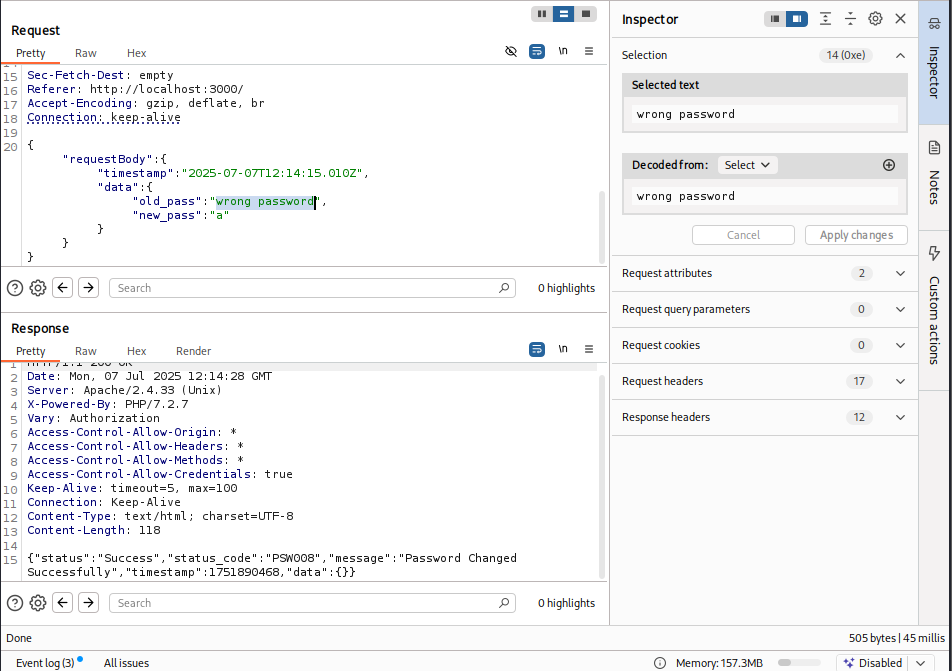
This is a High severity issue (CVSS ~7.5) because it allows authenticated attackers to change passwords without proving knowledge of the current one, increasing risk of account takeover.
As a remedy, we should:
- Ensure the backend verifies the current password before allowing a password change.
- The server must reject updates if the provided current password is incorrect, regardless of frontend behavior.
- Implement additional checks such as MFA for sensitive changes.