snmp-exploitation-techniques
This section explores security vulnerabilities in SNMP, specifically within versions SNMPv1 and SNMPv2c, which are widely used but inherently insecure due to lack of encryption and authentication. In a real-world setting, these weaknesses can be exploited to gain unauthorized access to sensitive network information or to launch more advanced attacks. The following subsections demonstrate how attackers can eavesdrop on SNMP traffic and perform brute force attacks to discover community strings.
1 Eavesdropping on SNMP Traffic
1.1 Overview of SNMPv1/v2c Vulnerabilities
SNMPv1 and SNMPv2c transmit all management traffic—including community strings and system information—in plaintext over UDP (port 161). This creates a significant security risk, particularly on networks where SNMP traffic is not isolated or encrypted. If an attacker gains access to a network segment where SNMP queries are being sent, they can intercept and analyze the data to:
- Retrieve device metadata (model, OS version, hostname)
- Discover SNMP community strings
- Map network device hierarchies and topologies
- Passively collect sensitive metrics over time
These vulnerabilities highlight why SNMPv3 is recommended in any security-conscious environment.
1.2 Capturing SNMP Packets Using Wireshark or tcpdump
To simulate an attacker monitoring SNMP traffic, packet capturing tools like Wireshark and tcpdump can be used.
Wireshark:
- Open Wireshark and select the appropriate network interface.
- Apply the following capture filter to isolate SNMP traffic:
udp.port == 161 - Initiate SNMP traffic by querying a device (e.g., using snmpwalk from another terminal).
- Examine captured packets. Under the SNMP protocol section, the community string will be clearly visible, as well as the OID being queried and the returned values.
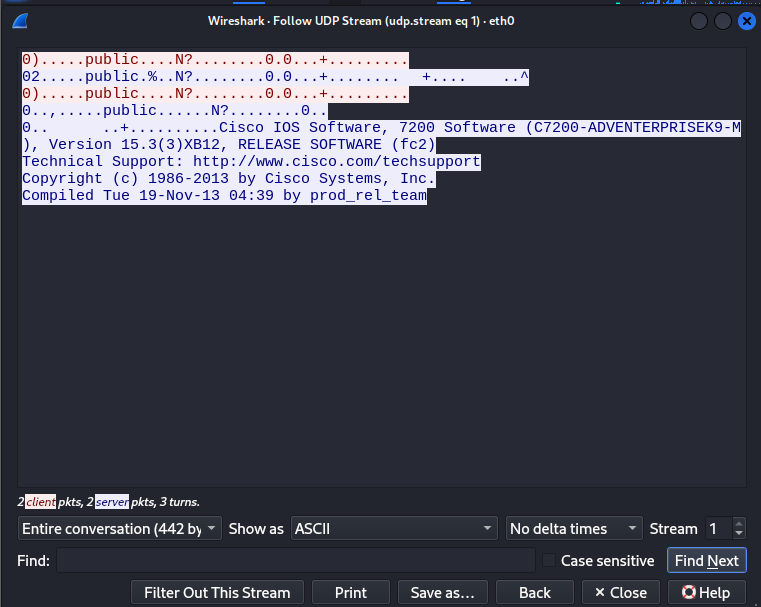
1.3 Analyzing Captured Community Strings
Within the captured packets, look for the community field. For example:
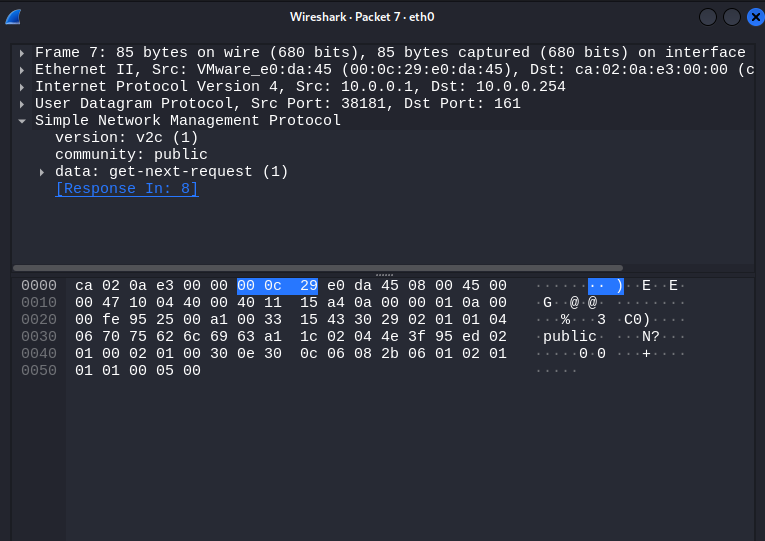
The community string (in this case, “public”) can then be reused by an attacker to issue their own SNMP queries and gather more information about the device, including:
- Running configurations
- Interface traffic stats
- Routing tables
- Device uptime and version information
This type of passive data collection is often the first stage in a targeted attack against network infrastructure.
2 Brute Forcing SNMP Community Strings
2.1 Introduction to SNMP Brute Force Attacks
When community strings are not known, attackers often turn to brute forcing—attempting many possible strings in rapid succession to identify valid ones. Since SNMPv1/v2c lacks any form of rate limiting or authentication lockout, it is highly susceptible to this method of enumeration.
Read-only access is often enough to map an entire network, while read-write access can lead to dangerous configuration changes or disruption of services.
2.2 Common Tools for SNMP Enumeration and Brute Forcing
1. onesixtyone
A lightweight and fast SNMP scanner that tests multiple community strings across multiple hosts simultaneously.
2. snmp-check
A tool designed to extract detailed information from SNMP-enabled devices. Once a valid community string is found, it can output interface lists, routing tables, ARP caches, and more.
3. snmpenum
Used for detailed enumeration and footprinting of SNMP-enabled hosts.
4. nmap SNMP scripts
The snmp-brute and snmp-info scripts within Nmap can also be used to discover valid community strings and gather device info.
2.3 Brute Force Demonstration Using onesixtyone
Prepare the following two files:
community.txt – contains a list of common or suspected community strings. targets.txt – contains the IP addresses of devices to test.
Run the scan:
onesixtyone -c community.txt -i targets.txtSample output:
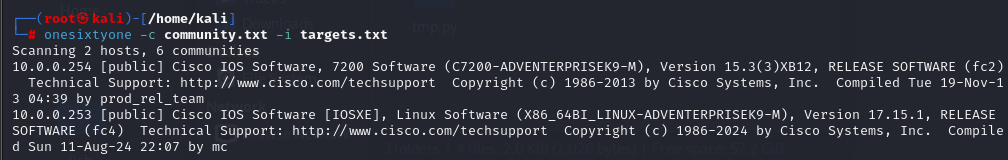
Once valid community strings are identified, tools like snmpwalk can be used to further enumerate the target.
2.4 Mitigation Strategies
To protect SNMP-enabled infrastructure from brute force and eavesdropping attacks, the following measures should be implemented:
- Disable SNMPv1 and SNMPv2c: Migrate to SNMPv3 wherever possible, which introduces user-based authentication and encryption.
- Restrict SNMP Access:
- Use Access Control Lists (ACLs) to limit SNMP access to trusted IP addresses only.
- Segment management traffic using VLANs or a separate management interface.
- Enforce Strong Community Strings:
- Avoid default strings like public and private.
- Use long, randomized strings that are rotated periodically.
- Monitor and Alert:
- Set up alerts for unusual SNMP activity such as repeated failed queries or access from unknown hosts.
- Firewall Rules:
- Block inbound UDP/161 traffic at perimeter firewalls unless explicitly required.