securing-file-transfers-with-sftp
5.1 Setting Up SFTP
SFTP (Secure File Transfer Protocol) is a secure alternative to FTP, providing encrypted file transfer capabilities. Unlike FTP, which transmits data in plaintext, SFTP ensures that all data transferred between the client and server is encrypted, preventing unauthorized access and man-in-the-middle (MITM) attacks.
To configure SFTP, you’ll first need to ensure that SSH (Secure Shell) is installed and configured on the server. SSH serves as the foundation for SFTP, as SFTP relies on SSH for secure communication.
1. Install and Configure SSH (if not already installed)
If SSH isn’t already installed on your server, you’ll need to install the OpenSSH server:
sudo apt update
sudo apt install openssh-serverOnce installed, we should enable SSH and the service can be checked using:
sudo systemctl start ssh
sudo systemctl status ssh2. Restrict SFTP Access for a Specific User
Next, you will configure the SSH server to only allow SFTP access for specific users, and optionally, restrict them to specific directories (like their home directories).
To do this, we’ll modify the SSH configuration file (/etc/ssh/sshd_config).
- Edit the SSH configuration file:
sudo nano /etc/ssh/sshd_config- Add the following configurations:
Subsystem sftp internal-sftp
# Restrict SFTP access to the user "sftpuser"
Match User sftpuser
ChrootDirectory /home/sftpuser
ForceCommand internal-sftp
AllowTcpForwarding no- Subsystem sftp internal-sftp: This line specifies that the internal SFTP server should be used, which is provided as part of the OpenSSH package.
- Match User sftpuser: This matches a specific user (sftpuser in this case) and applies the subsequent settings only to that user.
- ChrootDirectory /home/sftpuser: This restricts the user to a specific directory. The user can only access files within their home directory (/home/sftpuser), and they cannot move outside this directory.
- ForceCommand internal-sftp: This ensures that the user can only use the SFTP subsystem and cannot execute arbitrary commands on the server.
- AllowTcpForwarding no: This disables TCP forwarding for the user, further restricting their ability to use SSH for anything other than SFTP.
- Restart the SSH service to apply the changes:
sudo systemctl restart ssh3. Testing SFTP Access
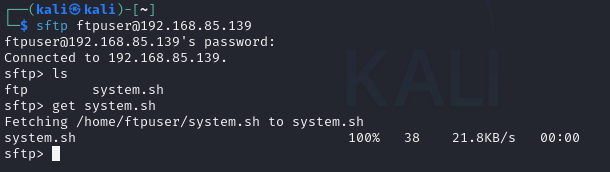
Once the configuration is complete, you can test the SFTP connection by trying to log in as the sftpuser:
sftp sftpuser@<server-ip>This command connects to the server using SFTP, and it should prompt for the sftpuser’s password. After logging in, the user will only have access to their ChrootDirectory, typically /home/sftpuser, and will be unable to access other parts of the system.
5.2 Demonstrating Encrypted Communication
One of the primary advantages of SFTP over FTP is encryption. In SFTP, both the command channel (where commands such as put or get are sent) and the data channel (where file transfers occur) are encrypted. This prevents eavesdropping and ensures that any credentials or files exchanged are not exposed to attackers.
Here’s how to demonstrate this:
- SFTP Connection Example:
sftp sftpuser@<server-ip>Upon initiating the connection, you’ll notice that the entire communication, including login credentials and file data, is encrypted. While using a network monitoring tool like Wireshark, you’ll find that the data being transmitted is not readable or in plaintext.
- Capturing the Encrypted Traffic:
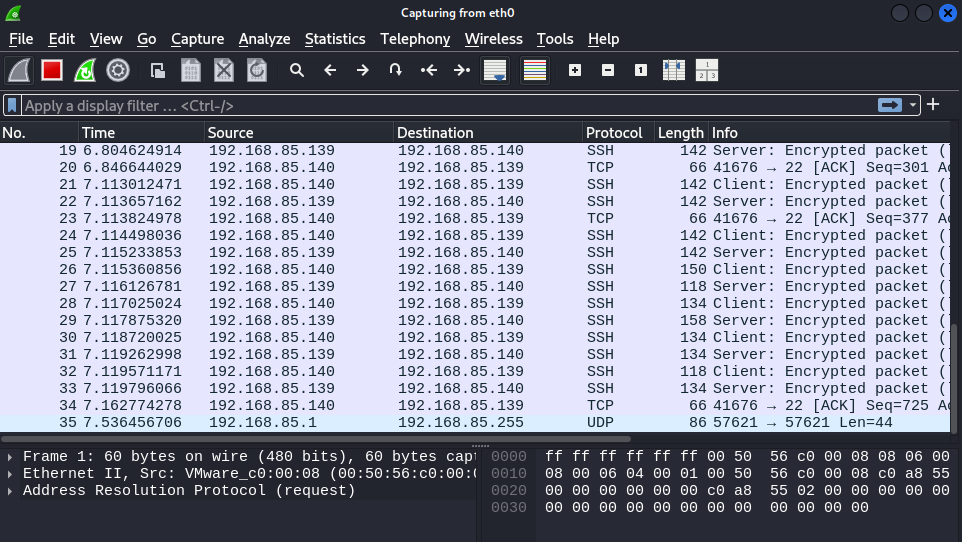
In a real-world scenario, an attacker may attempt to capture traffic between the client and the server using a packet sniffer (like Wireshark). However, since SFTP uses SSH encryption, the captured packets will be unreadable, ensuring the confidentiality of the communication.