demonstrating-ftp-vulnerabilities
1 Understanding Plaintext Transmission in FTP
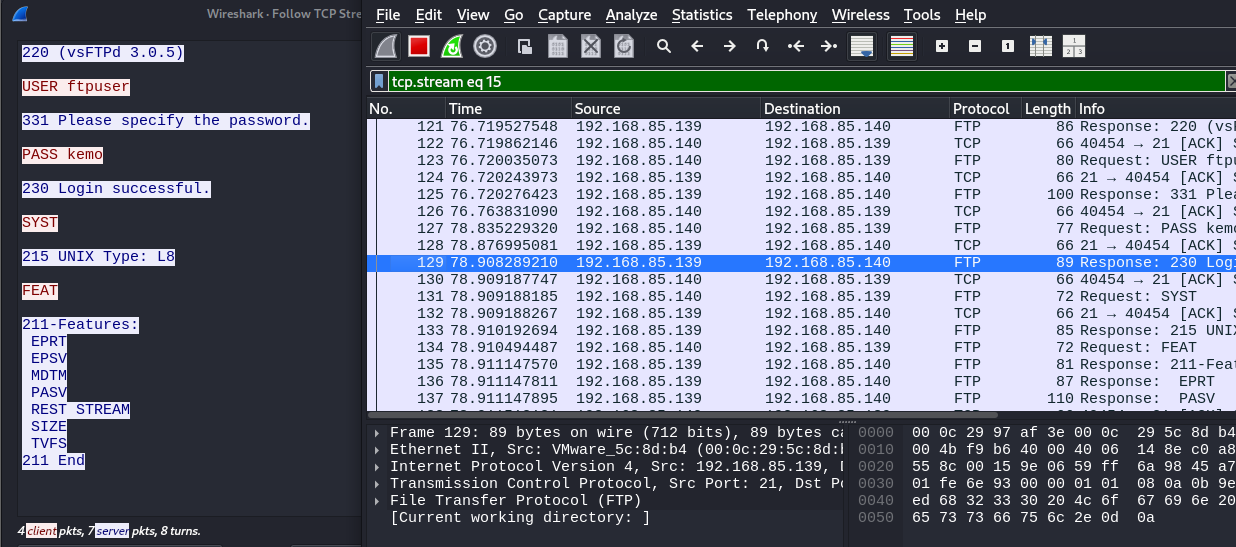
FTP transmits data, including usernames and passwords, in plaintext, making it highly susceptible to interception. Any attacker with access to the network can capture these credentials using packet-sniffing tools. This security flaw highlights the necessity of encrypted alternatives like SFTP.
2 Intercepting Credentials (Packet Capture & Analysis)
- Start Wireshark on the attack machine:
sudo wireshark- Wireshark provides a graphical interface for packet analysis.
- Monitor FTP traffic while a user logs in.
- Observe captured packets and locate the credentials transmitted in plaintext.
- Use Wireshark’s Follow TCP Stream feature to extract login details. Analyze the captured data.
- The username and password should be visible in the packet contents.
- This step demonstrates why FTP should not be used for secure data transmission.